On the 19th of July 2024, an update of CrowdStrike caused a worldwide outage of all Windows-based systems, affecting hundreds of organizations across all industries. The problem lay within an update made to the CrowdStrike Falcon Cybersecurity platform, where it introduced a bug that eventually caused out-of-bounds memory read errors for the systems, ultimately crashing with the infamous Blue Screen of Death.
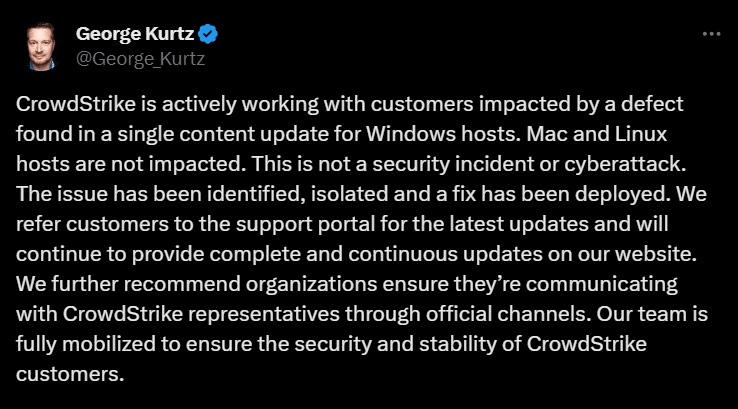
George Kurt (CEO, CrowdStrike Falcon) simply posted on his Twitter (X) handle by addressing issue that “It is identified, isolated and a fix patch is deployed“. Although it affected less than 1% of Windows devices, it grounded over 6% of flights and disrupted surgeries, broadcasts, money transfers, 911 call centers, and more.
CrowdStrike Overview and Connection with Microsoft
CrowdStrike, which is a leading US based cybersecurity company that holds a significant global market share. Their software “Falcon” offers advance threat detection and response capabilities by leveraging artificial intelligence and behavioural analysis to protect against malware, ransomware and other cyber threats.

Read Also: GPT-4o: Hype or Hope? Explore Latest Conversational AI
CrowdStrike’s Connection with Microsoft
CrowdStrike’s Falcon platform is closely integrated with Microsoft Windows, as it provides endpoint protection for Windows-based systems. This integration means that any updates or changes to the Falcon platform can directly impact Windows machines.
It is a lightweight agent that installs on Windows computers, continuously monitoring for threats and providing real-time detection and response capabilities. The integration with Windows allows Falcon to leverage deep system hooks to identify and mitigate threats effectively. However, this close integration also means that issues with Falcon updates can have significant repercussions for Windows users, as seen in the recent outage

Things that lead Windows Crash on Friday
CrowdStrike frequently updates their Falcon sensor with Rapid Response Content which includes the updated data on newly discovered hacking techniques. This Sensor then utilizes this information to monitor the installed device for any signs of breaches.
On a recent Friday morning, CrowdStrike released two updates. Despite being checked by an internal tool called the Content Validator which is supposed to automatically detect and block faulty updates, one problematic update slipped through and was released. This failure in the validation process led to the subsequent system crashes.
When the Falcon sensors received the update they tried to execute it using a built-in component called the Content Interpreter. This process threw “out-of-bounds” memory read error which occurs when a program tries to access an unauthorized section of the computer’s memory. This error was the root cause of the crashes experienced by the affected Windows systems.
Preventive Measures and Future Safeguards
Following the 19th July 2024 incident, CrowdStrike has outlined a series of measures to prevent similar occurrences in the future
Fraud to Teammates and Partners: UberEats Gift Card
After crash of millions of computers with careless update, CrowdStrike offered $10 Uber Eats gift card to the administrative team and partners for their effortless services to fix the bug. To apologize with their partners, Falcon creators sent them an email “To express their gratitude”.
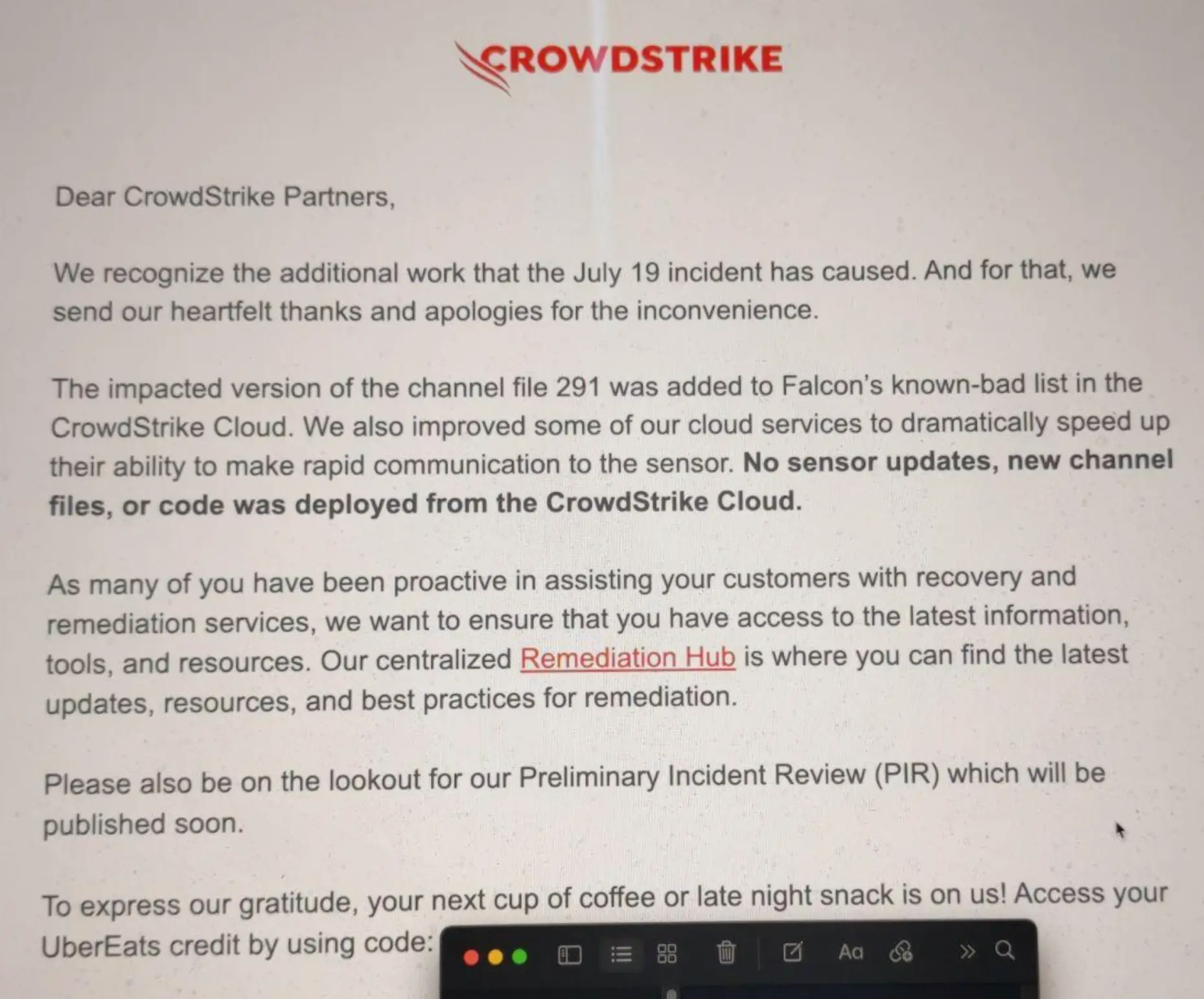
Many of people who received this email, went to redeem this voucher but unfortunately they received error from Uber Ear in which they said “Voucher has be cancelled issuing party and is no longer valid”.